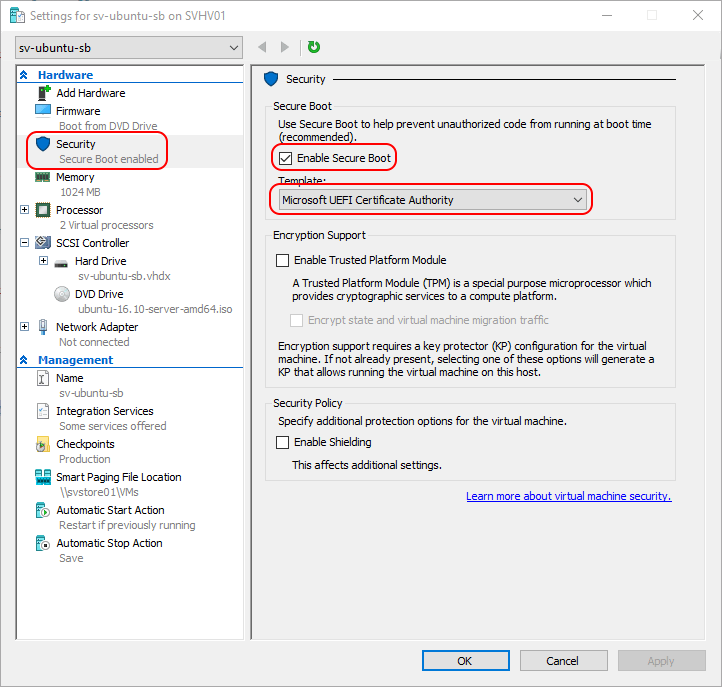
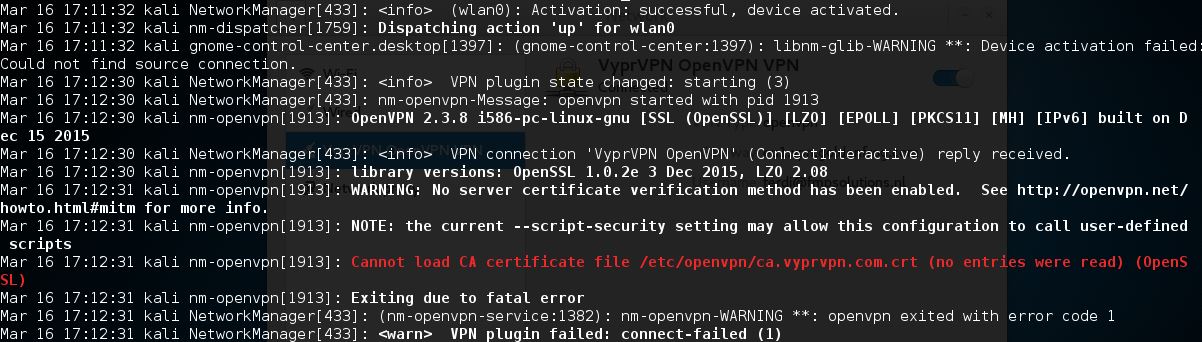
- Kali Linux Failed To Request New Sb Statement
- Kali Linux Failed To Request New Sb States
- Kali Linux Failed To Request New Sb State Farm
- Kali Linux Failed To Request New Sb State Park
Once you click Continue from the main installer failure screen ( Figure 4.26, “Installation Step Failed”), you will be returned to a screen that you will normally never see (the Main Menu shown in Figure 4.28, “Main Menu of the Installer”), which allows you to launch one installation step after another.
Hello and welcome on my blog, there Vijay Kumar,
This article about the ” Kali Linux configure network manually ” In this topic, I will cover all about the Kali Linux network configuration of LAN (Ethernet) and Wireless LAN adapter as well. After reading this article you will able to assign IP manually and by DHCP server as well.
Below are the current list of repositories on my Linux node root@node1 rpms# yum repolist Loaded plugins: fastestmirror, langpacks Loading mirror speeds from cached hostfile. base: centos.excellmedia.net. epel: repos.del.extreme-ix.org. extras: centos.excellmedia.net. openstack-stein: centos.excellmedia.net. updates: centos.excellmedia.net repo id repo name status base/7/x8664 CentOS-7. Once the machine is powered up, you will be prompted to s elect your preferred installation. Make sure that your Linux Distro converts to WSL2 if you want your Distro to operate under a full Linux Kernel. There is no harm in invoking Windows Update at this point. I recommend you do. Install the Windows Hypervisor Platform. (The likes of VMware and Virtual Box need it.) No harm in rebooting the computer at this point. Kali Linux: An installation step failed. You can try to run the failing item again from the menu, or slip it and choose something else. The failing step is.
Network interfaces (LAN adapter, wireless adapter, usb adapter, fast Ethernet) are responsible to connect and make communication between two or more computers in a network.
If the network card is not configured properly, then you are out of network and configuration is important for network security. The network should have proper IP Address, subnet mask, Default gateway, domain name server, etc.
So configure the network and get into the network. but the most important question:
How do you check the Kali Linux network configuration?
There are different methods for windows and Linux operating systems. Here we are discussing Kali Linux, I will explain tasks used in Linux. Following command is used to check the status of the networking cards in Kali Linux:
Before run command makes sure, you are working as root. I mean “You must be root to make changes in network configuration.
If you are checking only network configuration then you don’t have a need to be root.
$sudo ifconfig
$sudo ifconfig –a
You have seen the result of ifconfig command, You can see assigned IP address, MAC address, Netmask, for IPv4, etc.
You can run this command as a normal user, sudo user, or root user. If you didn’t create a normal user in Kali Linux then you are using the system by the root user.
Sometimes you find that network interface is not responding properly, you will have to enable and disable.
You have more than 1 interface, and you want to use only 1 adapter, then disable other adapters.
You can use Ifconfig command followed by up option and interface name to start the network interface and for stopping it use the down option.
You can use the following syntax to enable and disable network interface cards.
#ifconfig eth0 down
#ifconfig eth0 up
Assign IP Address for the network (eth0 or wlan0)
Eth0 is the number of a wired network interface card. if you want to assign IP address for wireless adapter replace eth0 by wlan0. The current configuration of this adapter can be changed by using the following command and this command will assign new IP address for your computer interface
$sudo ifconfig eth0 192.168.1.10
Kali Linux network configuration with IP address and Netmask
Netmask is used to indentify the network address. It can be configured by using given command. This will set the ip address 192.168.1.10 and set the subnet mask 255.255.255.0
$sudo ifconfig eth0 192.168.1.10 netmask 255.255.255.0
Add default gateway
Default gateway is added or changed, by using following command. It will set the default gateway 192.168.1.1
#route add default gw 192.168.1.1
OR
$sudo route add default gw 192.168.1.1
Add dns-namesevers

In Linux DomainName Server or DNS can be set or modifying the resolv.conf in the /etc directory. It can be changed by editing this file. add the following sytex in terminal
#echo nameserver 8.8.8.8 > /etc/resolv.conf
This command will remove the current nameserver and set 8.8.8.8. It can be added alternate nameserver by using following syntax
#echo nameserver 4.4.4.4 >> /etc/resolv.conf
Kali Linux network configuration from DHCP
Kali Linux Failed To Request New Sb Statement
DHCP services are one of the easiest ways to configure an Ethernet. A free DHCP server provides all required configuration settings for the network cards. Use the following method:
#leafpad /etc/networking/interfaces
make these entries
auto eth0
iface eth0 inet static
address {ip_Address}
netmask {netmask}
gateway {Default_gateway_IP_Address}
Save the file and exit to complete the modification. It is required to take down the network and again bring up Ethernet interfaces to applying this configuration.
Use the following command to configure the network adapter
#dhclient eth0
This will configure the network adapter using the settings provided by the DHCP Server.
How to configure network adapter in Kali LinuxHow to configure network adapter in Kali Linux by Command line
Posted by Cyber Pratibha on Thursday, 16 March 2017If Appreciate My Work, You should consider:
- Join Group for Discussion Facebook Group
- Get your own self-hosted blog with a Free Domain at ($2.96/month)
- Buy a Coffee to Us! Make Small Contribution by Paypal
- Support us by taking our :Online Courses
- Contact me :[email protected]
In our previous IPTables firewall series article, we reviewed how to add firewall rule using “iptables -A”.
We also explained how to allow incoming SSH connection. On a high-level, it involves following 3 steps.
- Delete all existing rules: “iptables -F”
- Allow only incoming SSH: “iptables -A INPUT -i eth0 -p tcp –dport 22 -j ACCEPT”
- Drop all other incoming packets: “iptables -A INPUT -j DROP”
The above works. But it is not complete. One problem with the above steps is that it doesn’t restrict the outgoing packets.
Default Chain Policy
The default policy of a chain is ACCEPT. If you don’t what what a chain means, you better read our iptables introduction article. So, both the INPUT and OUTPUT chain’s default policy is ACCEPT. In the above 3 steps we dropped all incoming packets at the end (except incoming ssh). However, we didn’t restrict the outgoing traffic.
As you notice below, it says “(policy ACCEPT)” next to all the three chain names (INPUT, OUTPUT, and FORWARD). This indicates that the default chain policy is ACCEPT.
So, you have two options here.
Option 1: Add drop rules
At the end, add the following three drop rules that will drop all incoming, outgoing, and forward packets (except those that are defined above these three rules). If you do this, the default chain policy is still ACCEPT, which shouldn’t matter, as you are dropping all the packets at the end anyway.
Option 2: Change the default chain policy to DROP
At the beginning, execute the following three commands that will change the chain’s default policy to DROP.
Now, if you add the allow ssh rule: “iptables -A INPUT -i eth0 -p tcp –dport 22 -j ACCEPT”, and do iptables -L, you’ll notice that it says “(policy DROP)” next to all the three chains.
But there is a problem here. The allow ssh incoming connection rule will not work anymore, because all the outgoing packets are dropped.
Allow Incoming Connections
When the default policy is DROP for INPUT and OUTPUT chains, for every incoming firewall rule, you need to specify the following two rules.
- Request rule: This is the request that comes from the client to the server for the incoming connection.
- Response rule: This is for the response that goes out from the server to the client (for the corresponding incoming request).
Example 1: Allow incoming SSH connection
This is to allow SSH connection from outside to your server. i.e You can ssh to your server from outside.
This involves two steps. First, we need to allow incoming new SSH connections. Once the incoming ssh connection is allowed, we also need to allow the response back for that incoming ssh connection.
First, Allow incoming SSH connection request, as shown below.
In the above example:
- iptables -A INPUT: Append the new rule to the INPUT chain. For incoming connection request, this always has to be INPUT.
- -i eth0: This refers to the input interface. For incoming connections, this always has to be ‘-i’.
- -p tcp: Indicates that this is for TCP protocol.
- –dport 22: This refers to the destination port for the incoming connection. Port 22 is for ssh.
- -m state: This indicates that the “state” matching module is used. We’ll discuss more about “-m” option (and all available matching modules for iptables) in future article.
- –state NEW, ESTABLISHED: Options for the “state” matching module. In this example, only NEW and ESTABLISHED states are allowed. The 1st time when a SSH connection request is initiated from the client to the server, NEW state is used. ESTABLISHED state is used for all further request from the client to the server.
Next, Allow outgoing (ESTABLISHED state only) SSH connection response (for the corresponding incoming SSH connection request).
In the above example:
- iptables -A OUTPUT: Append the new rule to the OUTPUT chain. Since this is for the response rule (for the corresponding incoming request) that goes out from the server, this should be OUTPUT.
- -o eth0: This refers the output interface. For outgoing connections, this always has to be ‘-o’.
- -p tcp: Indicates that this is for TCP protocol.
- –sport 22: This refers to the source port for the outgoing connection. Port 22 is for ssh. Since the incoming request (from the previous rule) came to the “destination” port, the outgoing response will go through the “source” port.
- -m state: This indicates that the “state” matching module is used.
- –state ESTABLISHED: Since this is a response rule, we allow only ESTABLISHED connection (and not any NEW connection).
Example 2: Allow incoming HTTP connection
This is to allow HTTP connection from outside to your server. i.e You can view your website running on the server from outside.
Kali Linux Failed To Request New Sb States
Just like the above SSH incoming rules, this also involves two steps. First, we need to allow incoming new HTTP connection. Once the incoming HTTP connection is allowed, we need to allow the response back for that incoming HTTP connection.
First, Allow incoming HTTP connection request, as shown below.
Next, Allow outgoing (ESTABLISHED only) HTTP connection response (for the corrresponding incoming SSH connection request).
Note: In the above HTTP request and response rule, everything is same as the SSH example except the port number.
Allow Outgoing Connections
When the default policy is DROP for the INPUT and OUTPUT chains, for every outgoing firewall rule, you need to specify the following two rules.
- Request rule: This is the request that goes out from the server to outside for the outgoing connection.
- Response rule: This is for the response that comes back from the outside to the server (for the corresponding outgoing request).
Example 3: Allow outgoing SSH connection
This is to allow SSH connection from your server to the outside. i.e You can ssh to outside server from your server.
This involves two steps. First, we need to allow outgoing new SSH connection. Once the outgoing ssh connection is allowed, we also need to allow the response back for that outgoing ssh connection.
First, Allow outgoing SSH connection request, as shown below.
Kali Linux Failed To Request New Sb State Farm
In the above example:
- iptables -A OUTPUT: Append the new rule to the OUTPUT chain. For outgoing connection request, this always has to be OUTPUT.
- -o eth0: This refers the output interface. For outgoing connections, this always has to be ‘-o’.
- -p tcp: Indicates that this is for TCP protocol.
- –dport 22: This refers to the destination port for the outgoing connection.
- -m state: This indicates that “state” matching module is used.
- –state NEW, ESTABLISHED: Options for the “state” matching module. In this example, only NEW and ESTABLISHED states are allowed. The 1st time when a SSH connection request is initiated from the server to the outside, NEW state is used. ESTABLISHED state is used for all further request from the server to the outside.
Next, Allow outgoing (ESTABLISHED only) SSH connection response (for the corresponding incoming SSH connection request).
In the above example:
- iptables -A INPUT: Append the new rule to the INPUT chain. Since this is for the response rule (for the corresponding outgoing request) that comes from the outside to the server, this should be INPUT.
- -i eth0: This refers the input interface. For incoming connections, this always has to be ‘-i’.
- -p tcp: Indicates that this is for TCP protocol.
- –sport 22: This refers to the source port for the incoming connection. Since the outgoing request (from the previous rule) went to the “destination” port, the incoming response will come from the “source” port.
- -m state: This indicates that the “state” matching module is used.
- –state ESTABLISHED: Since this is a response rule, we allow only ESTABLISHED connection (and not any NEW connection).
Putting it all together
Create rules.sh shell script which does the following:
- Delete all existing rules
- Set default chain policies
- Allow inbound SSH
- Allow inbound HTTP
- Allow outbound SSH
First, create the rules.sh
Kali Linux Failed To Request New Sb State Park
Next, execute the rules.sh and view the rules.
Using this as a basis you should be able to write your own incoming and outgoing iptables firewall rules. There is lot more to cover in IPTables. Stay tuned!
Previous articles in the iptables series: